Java architecture interview questions: We have compiled most frequently asked Java J2EE Interview Questions which will help you with different expertise levels.
Java J2EE Interview Questions on Architecture
Question 1.
What was the underlying need for J2EE? Elaborate.
Answer:
With the onset of web-centric applications that grew more dependent than ever on server-side technologies such as middleware, information technology departments of corporations needed a sustainable way to develop applications and related middleware that was both portable as well as scalable. These applications need to be designed to handle thousands of users simultaneously 24 hours a day, seven days a week, without any downtime. One of the major challenges to building such a complex application is to be able to design and test it.
J2EE simplifies the creation of enterprise-wide applications since the functionality is encapsulated in components of J2EE. This enables designers and programmers to organize the application into functionality that is distributed across the server-side components built using J2EE. Furthermore, J2EE is a versatile technology since application components built using J2EE are able to communicate with each other behind the scenes using standard communication methods such as HTTP, SSL, HTML, XML, RMI, and IIOP.
All J2EE programs are written in Java enabling a corporation to use its existing staff of Java programmers to create programs that work at each layer of the multi-tier infrastructure. J2EE contains all the interfaces and libraries to handle multithreading and synchronization as well. Java Beans, Java Servlets, and JavaServer Pages are core components of J2EE. In addition, J2EE consists of seven more standard services, all of which increase its usefulness and contribution to the industry.
Question 2.
Explain and elaborate on the J2EE multi-tier architecture.
Answer:
J2EE is a four-tier architecture (refer to Figure 16) consisting of the Client Tier (also referred to as the Presentation or Application Her), Web Tier, Enterprise JavaBeans Tier (also referred to as Business Her), and the Enterprise Information Systems Her. Each tier is focused on providing a specific type of functionality to an application. It’s important to delineate between functionality and physical location. Two or more tiers can physically reside on the same Java Virtual Machine (JVM) although each tier provides a different type of functionality to a J2EE application.
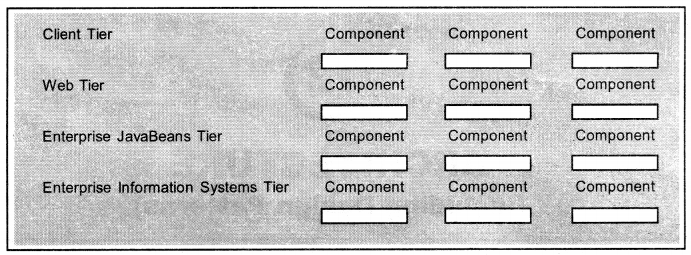
And, since the J2EE multi-tier architecture is functionally centric, a J2EE application accesses only tiers whose functionality is required by the J2EE application. It’s also important to disassociate a J2EE API with a particular tier, i.e. some APIs (that is, XML API) and J2EE components can be used on more than one tier while others APIS (that is, Enterprise JavaBeans API) are associated with a particular tier.
The Client Tier consists of programs that interact with the user. These programs prompt the user for input and then convert the users’ responses into requests that are forwarded to software on a component that processes the request and returns results to the client program. The Web Tier provides Internet functionality to a J2EE application. Components that operate on the Web Tier use HTTP to receive requests from and send responses to clients that could reside on any tier fa client being any component that initiates a request). The Enterprise JavaBeans Tier contains the business logic for J2EE applications. It’s here that where one or more Enterprise JavaBeans reside, each encoded with business rules that are called upon indirectly by clients.
Although an Enterprise JavaBean can access components on any tier, typically an Enterprise JavaBean accesses components and resources such as DBMS on the Enterprise Information System (EIS) tier. The EIS links a J2EE application to resources and legacy systems that are available on the corporate backbone network. It’s on the EIS inhere a J2EE application directly or indirectly interfaces with a variety of technologies including DBMS and mainframes which are part of the mission-critical systems that keep the corporation operational Components that work on the EIS communicate to resources using CORE A or Java connectors, referred to as J2EE Connector Extensions.
Question 3.
What do you understand by design patterns?
Answer:
By design patterns, we mean certain standard solutions for certain common problems which occur while designing a software system, e.g. whenever we want to restrict an application to create only one instance of a class, we make use of the Singleton Design Pattern.
Question 4.
Elucidate the Singleton Design Pattern.
Answer:
As already mentioned in the previous question, the Singleton Design Pattern is made use of whenever we need to design a class which can just one instance. The Singleton design pattern is very useful from the software engineering point of view.
The rules for creating the Singleton class are:-
(1) Constructor should be protected (it could be made private to prevent inheritance).
(2) Declare a static “self” pointer to hold a reference to the single instance of the class when it is created and initialize it to null.
(3) Declare a static “instance” function which creates and returns the newly created instance of the class when the static “self” pointer is null, otherwise, it returns the previously created instance.
(4) Declare a protected destructor that deletes the “self” pointer.
Question 5.
What do you understand by design principles?
Answer:
Design principles provide certain rules that an Object-Oriented software designer should keep in mind during the software design phase in order that:-
- each module/class is zero or less dependent on other modules/classes; and,
- each module/class is less affected by frequent requirement changes.
Question 6.
What is the Open-Closed Principle (OCP)?
Answer:
The OCP states that – “A module should be open for extension, but closed for modification”.
Question 7.
What is the Liskov Substitution Principle (LSP)?
Answer:
The LSP states that – “Subclasses should be substitutable for their superclasses; derived classes should be substitutable for their base classes”. Thus, a user of a base class should continue to function properly even if a derivative of that superclass is passed to it.
Question 8.
How would you go about writing a singleton in EJB?
Answer:
As already elaborated, a singleton is a very useful design pattern in software engineering. In a nutshell, a singleton is a single instantiation of a class with one global point of access. You would normally create a singleton in Java by using the ‘static’ keyword when defining a class.
However, one restriction of EJB is that you cannot use static fields in your beans. This precludes the use of the singleton design pattern. But, if you still have to use a singleton, here are a couple of strategies:-
- Limit the pool size
- Use RMI-IIOP and JNDI
Question 9.
Explain briefly the JNDI architecture.
Answer:
JNDI is made up of two halves: the client API and the Service Provider Interface (SPI). The client API allows your Java code to perform directory operations. This API is uniform for all types of directories. You will spend most of the time using the client API. The JNDI SPI is a framework for JNDI implementers: an interface that implementations of naming and directory services can be plugged into. The SPI is the converse of the API: while the API allows clients to code to a single unified interface, the SPI allows naming and directory service vendors to fit their particular proprietary protocols into the system, as shown in Figure 17. This allows client code to leverage proprietary naming and directory services in Java while maintaining a high level of code portability.
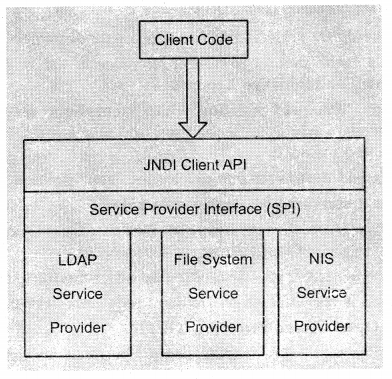
Question 10.
Can you elaborate on the similarities between JNDI architecture and JDBC?
Answer:
The JNDI architecture is somewhat like the Java Database Connectivity (JDBC) package in that:-
- In JDBC, one uniform client API performs database operations. In JNDI, naming and directory service clients invoke a unified API for performing naming and directory operations.
- In JDBC, relational database vendors provide JDBC drivers to access their particular databases. In JNDI, directory vendors provide service providers to access their specific directories. These providers are aware of specific directory protocols, and they plug into the JNDI SPI.
Question 11.
What do you understand by “design patterns” in general? Elucidate.
Answer:
Design patterns offer simple and elegant solutions to specific problems in object-oriented software design such as Java, C++, Smalltalk, and so on. They capture solutions that have developed and evolved over time. They reflect untold redesign and recoding as developers have struggled for greater reuse and flexibility in their software. Design patterns capture these solutions in a succinct and easily applied form. In other words, “design patterns” make it easier to reuse successful designs and architectures. Simply put, they help a designer get a design “right” faster!
Question 12.
What are the types of design patterns? Enumerate with suitable examples.
Answer:
There are, in general, three kinds of design patterns:-
- Creational, e.g. Abstract Factory, Factory Method, Singleton, Builder, and Prototype.
- Structural, e.g. Facade, Adapter, Bridge, Composite, Decorator, Flyweight, and Proxy.
- Behavioral, e.g. Chain of Responsibility, Command, Interpreter, Iterator, Mediator, Momenta, Observer, State, Strategy, Template Method, and Visitor.
Question 13.
Elaborate on the following design patterns as regards their applicability and consequences:
- Abstract Factory Creational Pattern;
- Factory Method Creational Pattern;
- Singleton Creational Pattern; and,
- Facade Structural Pattern
Answer:
Applicability
(a) The Abstract Factory pattern should be used when:
- A system is independent of how its products are created, composed, and represented;
- A system is configured with one of the multiple families of products;
A family of related product objects is designed to be used together, and you need to enforce this constraint; and, - You want to provide a class library of products, and you want to reveal just their interfaces, not their implementations. –
(b) The Factory Method pattern should be used when:
- A class cannot anticipate the class of objects it must create;
- A class wants its subclasses to specify the objects it creates;.and,
- Classes delegate responsibility to one of several helper subclasses, and you want to localize the knowledge of which helper subclass is the delegate.
(c) The Singleton creational pattern should be used when:
- There must be exactly one instance of a class, and it must be accessible to clients from a well-known access point; and,
- When the sole instance should be extensible by subclassing, and clients should be able to use an extended instance without modifying their code.
(d) Use the Facade structural pattern when:
- You want to provide a simple interface to a complex subsystem;
- There are many dependencies between clients and the implementation classes of abstraction; and,
- You want to layer your subsystems. Use a facade to define an entry point to each subsystem level.
Consequences
(a) The Abstract Factory pattern has the following benefits and liabilities:
- It isolates concrete classes;
- It makes exchanging product families easy;
- It promotes consistency among products, and 1
- Supporting new kinds of products is difficult.
(b) The Factory Method pattern has the following consequences:
- Provides hooks for subclasses; and,
- Connects parallel class hierarchies.
(c) The Singleton pattern has several benefits:
- Controls access to sole instance;
- It creates a reduced namespace;
- Permits refinement of operations and representation;
- Permits a variable number of instances; and
- More flexible than class operations.
(d) The Facade pattern has the following consequences:
- It shields clients from subsystem components, thereby reducing the number of objects that clients deal with and making the subsystem easier to use;
- It promotes weak coupling between the subsystem and its clients; and,
- It doesn’t prevent applications from using subsystem classes if they need to. Thus, you can choose between the ease of use and generality.
Question 14.
What is JAXB?
Answer:
JAXB (Java Architecture for XML Binding) is a popular data binding framework. It supports most XML Schema, excluding wildcards, notations, redefinitions, keys, and substitution groups. And, the binding is customizable.
Question 15.
Elucidate the Model-View-Controller (MVC) pattern.
Answer:
Web applications when seen as collections of JSP pages (or servlets) that the client navigates between referring to a design known as the Model 1 approach. For larger applications, this architecture is ad hoc. Instead, it is recommended to use the Model 2 approach, which is an instance of the Model-View-Controller (MVC) design pattern that dates back to GUI (Graphical User Interface) applications in the early Smalltalk-80 system.
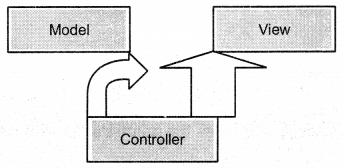
1. The MVC pattern distributes an application into three main parts: model, view, and controller.
2. The model encapsulates the data and accompanying operations (the business logic), and is typically programmed as Java classes, perhaps with an underlying database.
3. The view is typically a collection of JSP pages that interact with the model to present various data to the client.
4. The controller is written as a single servlet that handles all interactions with the client, updates the model, and selects appropriate views as responses.
5. The MVC pattern is often illustrated by the above general picture (Figure 18) wherein, the arrows indicate method invocations.
