We have compiled most frequently asked Java J2EE Interview Questions which will help you with different expertise levels.
Java J2EE Interview Questions on Networking
Question 1.
What is the client/server model in the context of networking?
Answer:
The term client/server is often heard in the context of networking. A server is anything that has some resource that can be shared. Thus, there are compute servers that provide computing power; print servers that manage a collection of printers; disk servers that provide networked disk space; and web servers which store web pages. And, a client is simply any other entity that wants to gain access to a particular server.
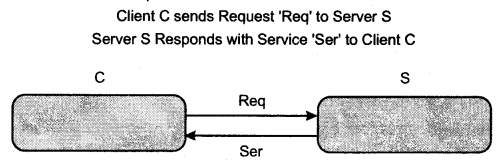
A network can have several clients and servers and this architecture is aptly called the client/ server architecture. Figure 2 shows a simple client/server model. In this simple model, it can be easily seen that the client sends a request to the server and the server responds upon receiving the request.
Question 2.
Elaborate on the advantages of a network.
Answer:
There is essentially one chief advantage that we derive by using a network, viz. it helps in the optimal utilization of the available system resources by making resource sharing possible amongst the connected systems on the network.
Question 3.
What do you mean by ‘throughput’?
Answer:
In computer parlance, throughput is the amount of work a computer network can perform during a given period of time.
Question 4.
What do you understand by a firewall?
Answer:
A firewall is simply a mechanism that isolates a network from the rest of the Internet, allowing only specific traffic to pass through it.
Question 5.
Why is data encryption required?
Answer:
Data traversing unsecured networks is open to many kinds of attacks. Data can be read, altered, or forged by anybody who has access to the route your data takes, e.g. a protocol analyzer (sniffer) can read packets and gain classified information, or, an intimidating party can tamper with packets and cause damage by hindering, reducing, or preventing network communications within your organization.
Encryption provides a means to safeguard network data that travels from one router to another across unsecured networks. Encryption is particularly important if certain confidential/critical data is being sent.
Question 6.
What do you understand by public-key encryption?
Answer:
Any cryptographic system essentially employs two keys for encryption/decryption, viz. the public key known to everyone and a private (secret) key known only to the recipient of the message. When device X wants to send a secure message to device Y, it uses device Y’s public key to encrypt the message. Device Y then uses its private key to decrypt the message sent by device X.
An important element to the public key system is that the public and private keys are related in such a manner that only the public key can be used to encrypt the messages and only the corresponding private key can be used to decrypt them. Moreover, it is virtually impossible to deduce the private key if you know the public key.
The only difficulty with public-key systems is that you must know the recipient’s public key to encrypt a message.
Question 7.
Elucidate digital signatures/certificates.
Answer:
Digital signatures/certificates are essentially attachments to an electronic message used for purposes of security. The most common use of digital certificates is to verify that a user sending a message is the one he/she claims to be and to provide the receiver with the means to encode a reply.
An individual wishing to send an encrypted message applies for a digital certificate from a Certificate Authority (CA). The CA issues an encrypted digital certificate containing the applicant’s public key and a variety of other identification information. The CA makes its own public key readily available through print publicity or perhaps on the Internet.
The recipient of an encrypted message uses the CA’s public key to decode the digital certificate attached to the message, verifies it as issued by the CA, and then obtains the sender’s public key and identification information held within the certificate. With this information, the recipient can send an encrypted reply.
The most widely used standard for digital certificates is X.509.
Question 8.
What is the use of the URLs?
Answer:
The Uniform Resource Locators (URLs) provide a reasonably intelligible form to uniquely identify/address information on the Internet.
Question 9.
What is the most widely used protocol on the Internet?
Answer:
hypertext transfer protocol (HTTP) is the most widely used protocol on the Internet. Using this protocol, the text from one machine to another is sent/received.
Question 10.
Why is Java suitable for the Internet?
Answer:
Java suits the Internet just about in the possible way. But, there are specifically two main reasons. First Java, the being system independent, is portable and can be run on any kind of system on the Internet. In other words, Java’s versatility is the mainstay of the Internet. And, secondly, Java with its strong type checking and lack of pointers is especially suitable for the Internet by eliminating most of the security concerns of the Internet.
Question 11.
What do you understand by a socket?
Answer:
A socket is essentially a connection point between a client and a server on the same network. t
Question 12.
Does the port number identify a socket uniquely?
Answer:
Yes! It does!!
Question 13.
What do you understand by IP address?
Answer:
An IP address is a unique identification number allotted to every computer on a network/Internet. It contains some unique bytes identifying the network and the actual inside the network.
Question 14.
What do you understand by DNS?
Answer:
DNS or Domain Naming Service, as it is called, is a service provided by the Internet that helps in mapping the IP addresses with their corresponding website names.
Question 15.
What is the full form of JSSE?
Answer:
Java Secure Socket Extension.
Question 16.
What are proxy servers?
Answer:
A proxy server speaks the client side of a protocol to another server. This is often required when clients have certain restrictions on which servers they can connect to. Thus, a client would connect to a proxy server, which did not have such restrictions, and the proxy server would, in turn, communicate for the client.
